OpenID Connect (OIDC) Authentication
- Configure your OIDC client for Authorization Code Flow
- Set the relevant fields in titra

- Client ID: Client ID as per your OIDC App Configuration
- Client Secret: As per your OIDC App Configuration
- OIDC Server Url: Your auth domain e.g. http://auth.your.domain
- Authorization Endpoint: /your/auth/endpoint Note the prepended slash
- Token Endpoint: /your/token/endpoint Note the prepended slash
- UserInfo Endpoint: /your/userinfo/endpoint Note the prepended slash
- Id Token Fields: Extra fields to be grabbed from your token and appended to the user. In my case my server returns an opaque access token which it grabs first (not the id token) so make sure that these fields are on the relevant token.
- Request Permissions: These permissions will be requested from your OIDC server, it defaults to openid,profile,email.
You can disable the default login form to prevent password based logins entirely:
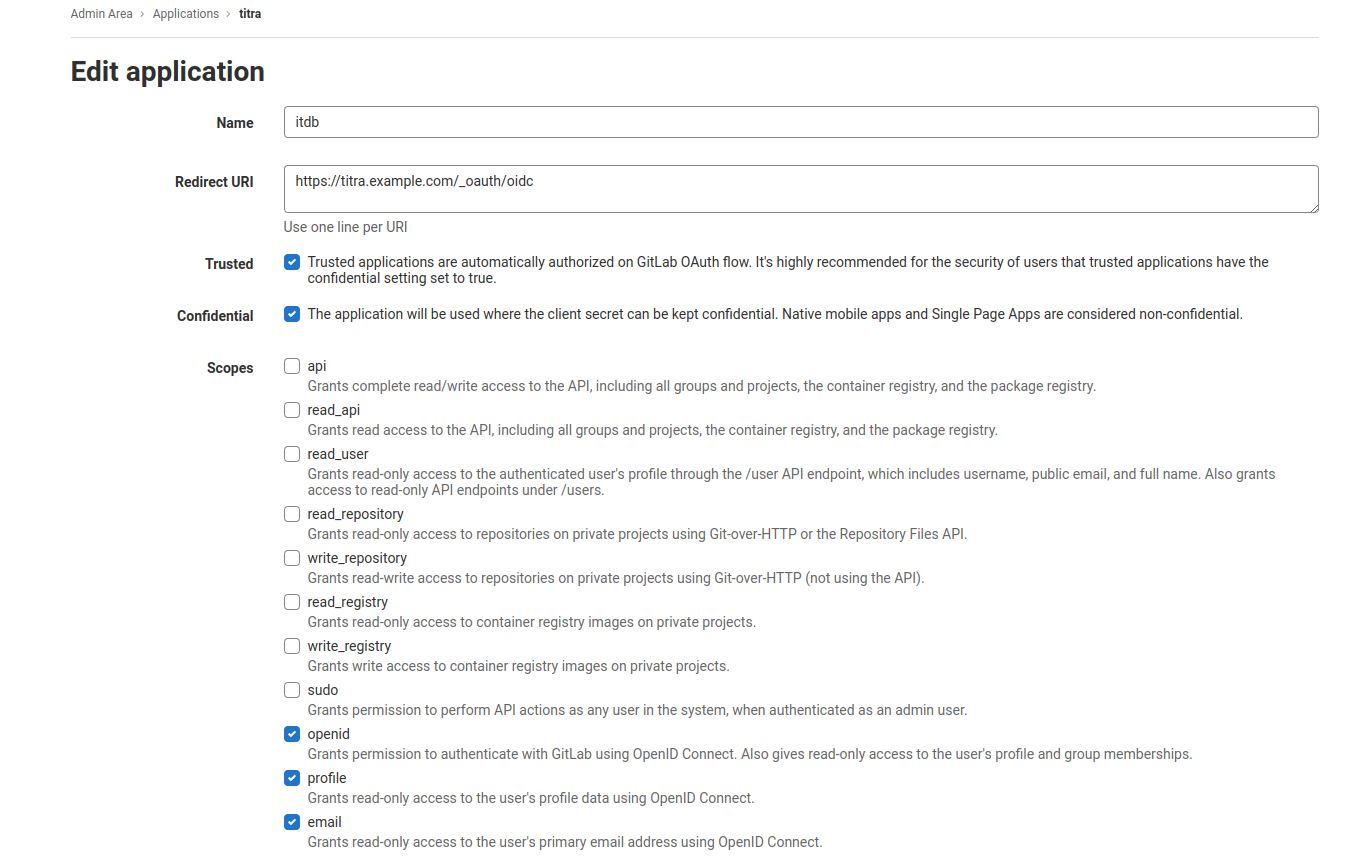
Gitlab OpenID Provider
Example configuration provided by Github user Rishats in issue 171.
All credit goes to @iamscottcab who has authored this documentation and provided two pull requests to improve the OIDC integration. Also a shoutout to @Rishats for providing the Gitlab example configuration!
No comments to display
No comments to display